Quantum Cryptography and the Looming Threat to AES-256: How Governments Are Collecting Data for Future Exploitation
Mwjohnson0 - https://creativecommons.org/licenses/by-sa/4.0
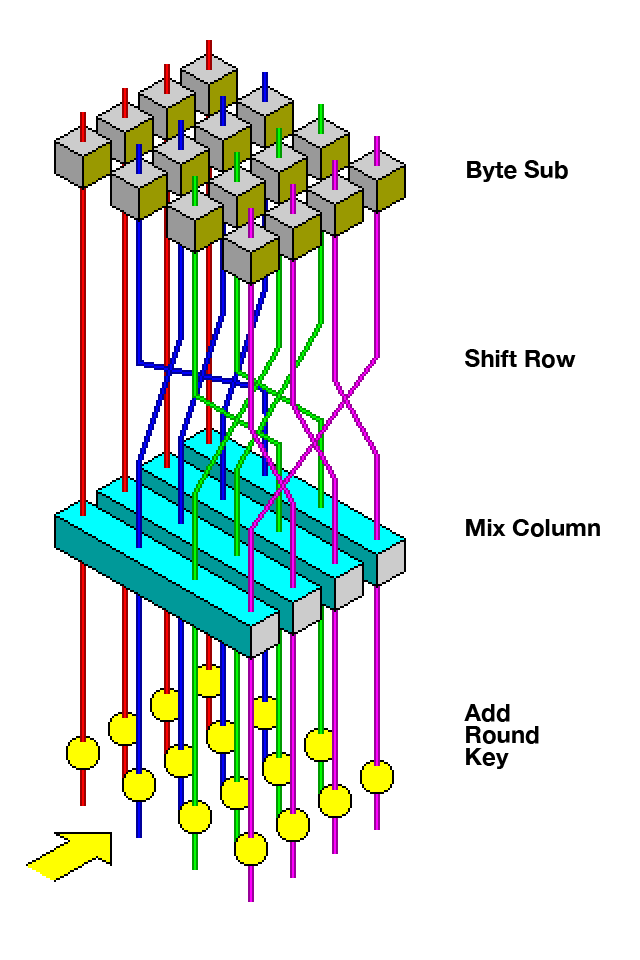
As the digital world grows ever more complex and interconnected, the security of data has become one of the most critical concerns of our time. From encrypted emails to secure financial transactions, the foundation of our digital privacy relies on encryption algorithms like AES-256 (Advanced Encryption Standard). For years, AES-256 has been the gold standard in encryption, widely trusted to secure sensitive information against even the most advanced cyber threats. For a deeper dive into the mechanics of AES-256 encryption, check out this excellent video by 3blue1brown.
However, a powerful new force is emerging—quantum computing. With the potential to break conventional encryption methods, quantum computers are poised to disrupt the entire cybersecurity landscape. Even today, there’s an alarming possibility that government agencies and nation-states are collecting and storing encrypted data, waiting for the day when quantum technology will be powerful enough to crack modern encryption schemes. This strategy, often referred to as "sniff and collect," could be the quiet prelude to a global cybersecurity crisis.
What is Quantum Cryptography?
Quantum cryptography leverages the principles of quantum mechanics to create encryption methods that, in theory, could be unbreakable. Unlike classical cryptographic systems, which rely on mathematical difficulty (such as factoring large numbers), quantum cryptography utilizes the properties of quantum particles, such as superposition and entanglement, to secure communications.
However, while quantum cryptography holds promise for the future, quantum computing also threatens current encryption methods. Classical encryption algorithms like AES-256 are based on the difficulty of solving certain mathematical problems, such as prime factorization or discrete logarithms. A sufficiently advanced quantum computer, using algorithms like Shor’s algorithm, could solve these problems exponentially faster than any classical computer.
AES-256: A Fortress Today, But for How Long?
AES-256 is widely regarded as uncrackable using today's classical computers. It would take billions of years for even the fastest supercomputers to brute-force their way through the 2^256 possible combinations of an AES-256 key. But quantum computers, leveraging their unique ability to process multiple states simultaneously, could theoretically reduce this timeframe to a matter of days or even hours.
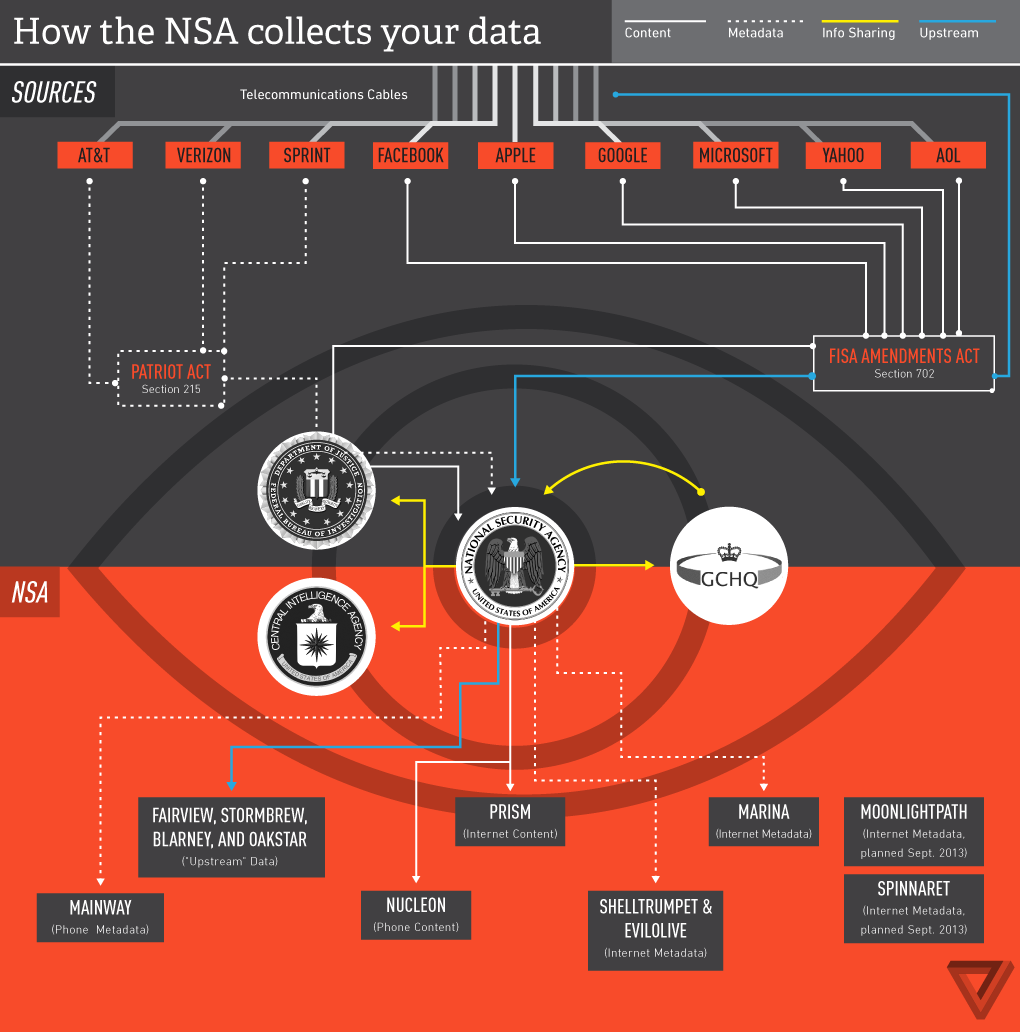
The threat of quantum computing breaking AES-256 is not just theoretical—it's something governments around the world are actively preparing for. In fact, many cybersecurity experts believe that nation-states are already engaged in massive data collection efforts, capturing encrypted communications and sensitive information with the intent of decrypting it once quantum computers become powerful enough.
The “Sniff and Collect” Strategy
The "sniff and collect" approach is exactly what it sounds like. Government agencies and cyber-intelligence organizations are intercepting and archiving massive amounts of encrypted data—emails, phone calls, financial transactions, and classified communications—knowing full well that they cannot decrypt this information now. The idea is to store this data until quantum computers mature to the point where they can easily break modern encryption algorithms like AES-256.
Many intelligence agencies, including the NSA, have been implicated in large-scale data collection programs, and the existence of these programs has been confirmed through high-profile leaks by whistleblowers like Edward Snowden. Stored now, cracked later is the mantra behind these operations, as they aim to capitalize on future technological advances in quantum computing to gain unprecedented access to sensitive information.
This potential quantum-powered decryption represents a ticking time bomb. What is collected today under the protection of AES-256 encryption could be exposed in the future, leading to severe consequences for privacy, national security, and the integrity of international communications.
Current Defenses with QKD and its Weak Spots
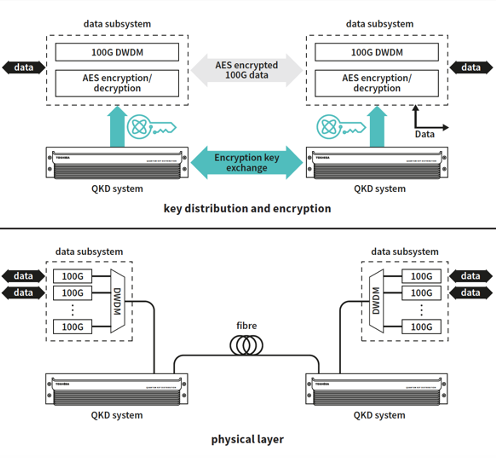
While the threat of quantum computing looms, Quantum Key Distribution (QKD) has emerged as a defense against the risks posed by quantum computers. QKD uses the principles of quantum mechanics to distribute cryptographic keys between parties securely. The security of QKD comes from the fact that any attempt to intercept or tamper with the quantum key would disturb the quantum state of the particles, immediately alerting both the sender and receiver to the intrusion.
However, despite its promise, QKD has limitations:
Range: Current QKD systems are highly sensitive to distance. They struggle to maintain secure communication over long distances, often requiring repeaters to extend the range, but these repeaters introduce new security risks.
Practicality: QKD requires specialized hardware, such as quantum-capable transceivers, making it expensive and impractical for widespread adoption across global communication networks. The infrastructure for QKD is still in its infancy and isn't ready for mass implementation.
Man-in-the-Middle Attacks: While QKD is theoretically secure, practical implementations have shown vulnerabilities to side-channel attacks, such as Trojan-horse attacks and blinding attacks, which target the physical devices used for QKD rather than the underlying quantum mechanics.
Integration: QKD only secures the key exchange process, meaning it still relies on conventional cryptographic algorithms (such as AES-256) for actual data encryption. Thus, it does not eliminate the risk that these algorithms will eventually be broken by quantum computing.
While QKD provides a short-term layer of defense, the long-term answer to the quantum threat lies in quantum-resistant cryptographic protocols that are immune to quantum attacks.
Quantum-Resistant Protocols: What NIST May Settle on This Year
Recognizing the quantum threat, the National Institute of Standards and Technology (NIST) launched a global competition to identify and standardize quantum-resistant cryptographic algorithms. These algorithms are designed to withstand attacks from both classical and quantum computers, ensuring that data encrypted with them remains secure, even in a post-quantum world.
NIST has narrowed the field and is expected to settle on the finalists for quantum-resistant protocols by the end of this year. Some of the leading candidates include:
Lattice-Based Cryptography: Lattice-based schemes, such as CRYSTALS-Kyber and CRYSTALS-Dilithium, are considered among the strongest contenders for post-quantum encryption. These schemes rely on the hardness of certain lattice problems, which are resistant to both classical and quantum attacks. They are seen as leading options for replacing AES-256 in the future.
Code-Based Cryptography: Protocols like Classic McEliece are based on the difficulty of decoding random linear codes. McEliece has been around since the 1970s and is widely regarded for its long track record of security. However, one of its drawbacks is that it requires relatively large key sizes compared to lattice-based methods.
Multivariate Polynomial Cryptography: Schemes like Rainbow rely on solving systems of multivariate quadratic equations, a problem that is difficult for both classical and quantum computers to solve. Rainbow is being considered for use in digital signatures but is less suited for general encryption.
Hash-Based Signatures: Algorithms like SPHINCS+ offer strong resistance to quantum attacks through the use of cryptographic hash functions. These are seen as useful in specific cases like digital signatures but are not practical for all cryptographic tasks due to their large signature sizes.
NIST’s final decision on quantum-resistant standards will mark a pivotal moment in the shift toward quantum-safe cryptography. These algorithms will need to be implemented widely and quickly, as quantum computers could render current encryption methods obsolete within the next decade.
Signal Messenger: Pioneering Post-Quantum Cryptography
While many applications have yet to adopt quantum-resistant encryption, the Signal messenger app is already ahead of the curve. In a recent blog post, Signal announced its implementation of Post-Quantum Extended Diffie-Hellman (PQXDH), which combines classical encryption algorithms with post-quantum algorithms to ensure future-proof secure communications.
Signal’s approach involves layering post-quantum key agreement protocols on top of existing cryptographic systems, making it one of the first mainstream messaging applications to take concrete steps toward mitigating quantum risks. The dual encryption structure not only preserves current security standards but also makes Signal more resilient against future quantum-based decryption attempts.
To read more about Signal’s post-quantum cryptography initiative, check out their detailed blog post.
When Will "Q-day" Arrive?
Opinions on when we will reach "Q-day"—the day when quantum computers are capable of breaking widely-used encryption methods—vary dramatically. Some experts predict that quantum computers capable of breaking AES-256 could be operational within the next 10-15 years, while others argue that we are still decades away from achieving such capabilities.
Optimistic projections suggest that within a decade, quantum computers with several thousand qubits will be able to solve meaningful problems, including breaking encryption. Companies like IBM and Google have made significant strides in developing quantum processors, but scaling these systems to the level needed for cryptographic attacks remains a substantial challenge.
However, pessimistic viewpoints hold that we are still at least 30 years away from a quantum computer capable of breaking AES-256. Building fault-tolerant quantum systems, which are necessary to prevent errors in calculations, is a complex task that quantum researchers have yet to solve fully. Nevertheless, the uncertainty surrounding the timeline means that the quantum threat should not be underestimated.
Conclusion
The race between encryption and decryption has always been a high-stakes game, but the advent of quantum computing raises the stakes to unprecedented levels. The era of sniff and collect is already upon us, with governments and nation-states preparing for a future where today’s most secure encryption methods could be shattered. While quantum cryptography offers hope for unbreakable encryption, the current reality is one of impending vulnerability.
The message is clear: What’s encrypted today might be decrypted tomorrow. Preparing for this future means staying ahead of the curve, embracing new quantum-safe encryption methods, and being aware of the broader geopolitical landscape where nation-states are poised to exploit the power of quantum computing. The quantum revolution is coming—are you ready for it?